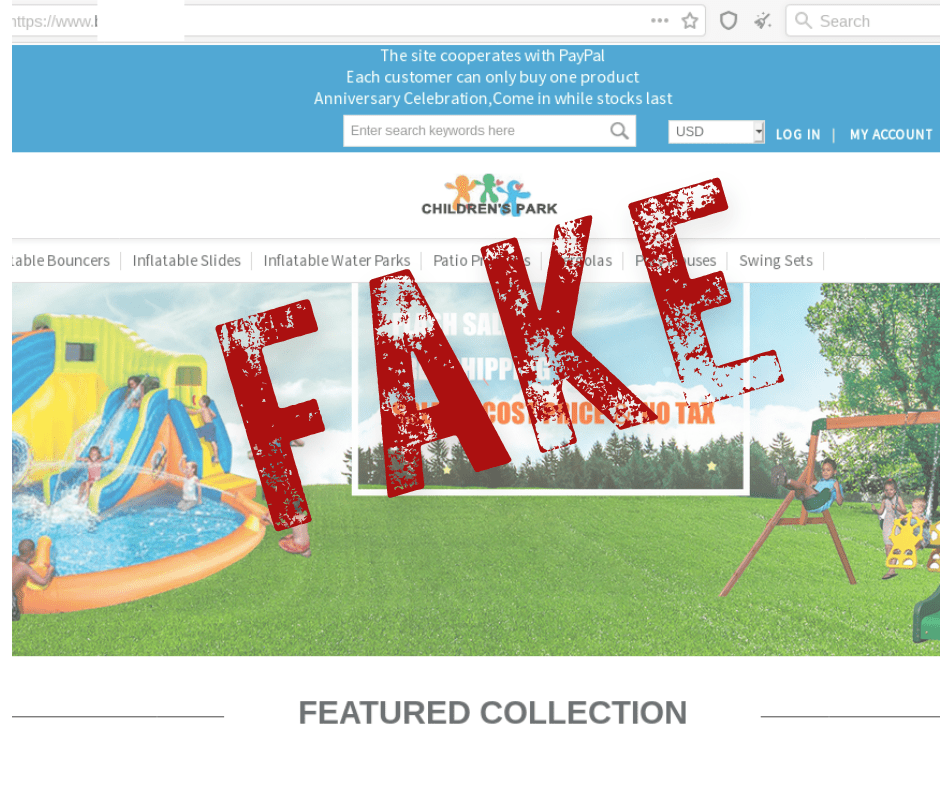
Yet Another Cybersecurity Prediction Article For 2022
As tradition in the InfoSec world dictates, it’s time for us to prognosticate what 2022 is going to look like with cyber attacks and other issues. Log4j As of right now, Log4j will be the gift that keeps on giving. To catch up on Log4j/log4shell stuff, check out our article that we’ve been updating. Because […]
Yet Another Cybersecurity Prediction Article For 2022 Read More »