Welcome to Bsquared Intel’s Ultimate Holiday Shopping Cybersecurity Guide 2! This is the updated guide for 2023 to what we originally put out a couple of years ago.
If you are one of the millions that will go shopping this Black Friday/Cyber Monday it’s a good time to keep your wits about you. Even if you’ve already started your holiday shopping, the cyber Grinches will be out. How do you navigate through this minefield of malicious shopping sites, phishing emails and texts, and too good to be true deals? In this holiday shopping guide we’ll be giving you some things to look out for while you’re shopping and if you’re a business owner things you can do to protect yourself and your customers.
Before we start, we’re going to give you a crash course in a few things as they are fundamental to how scams/phishing attacks work and issues related to malware.
Social engineering
At the core of a scam is social engineering.
A very basic definition of social engineering is framing someone’s reality in order to get them to do something you’ve already predetermined. Kids do this to parents. Let’s say their end goal is to stay up past their bed time or to have a snack. They’ll push all their parents’ buttons to succeed. In the cybercrime sense, there’s two optimal outcomes. 1) To get you to give up sensitive information like usernames/passwords, financial information, or other types of personal/sensitive information. 2) To get you to do something out of character. This includes getting you to, scan a QR code. or click on a link, or download an attachment that’s malicious, to install an untrusted app, to get you to enter suspicious commands into a command prompt, or to give them physical access to a building or a sensitive area.
At the center of a social engineering attack are a few elements:
- They exploit your emotions. The goal is to get you to have a knee-jerk reaction and not think logically about the social engineer’s request.
- There’s always a time component to their requests. This is to get you to rush, make mistakes, and prevent you from slowing down to see what’s really going on.
- Use/abuse of authority. The bad actor may pose as a legal authority. You typically see this play out in IRS email scams where the scammer is pretending to be an IRS agent who has the power to levy fines or impose jail time for your non-compliance. There’s also authority of an industry. That might look like someone posing as Amazon, Walmart, Microsoft, Apple, PayPal, your bank, and other businesses you frequent. There’s also what we would like to label as organizational authority. This is someone posing as the CEO, president, director, manager, or someone who has the authority to compel you to do something at work under the threat of being fired if you don’t comply.
With the focus of this article being the holiday shopping season, and by extension helping out charities, the more frequent forms of social engineering you’ll come across are:
- Phishing emails
- Phishing texts (AKA SMiShing)
- Voice phishing (AKA Vishing)
- QR Code phishing (AKA Quishing) (This is an emerging threat that you may start encountering more frequently.)
- Fake websites
- Fake social media profiles
Later on we’ll be giving you a few examples of things we’ve found in the wild and break things down a little so that you know what to look out for. For now we’ll move on to malware.
Malware
Malware is malicious software. Broadly, malware allows a bad actor to either snoop on you or to destroy things. If we want to get fancy, malware allows for espionage or sabotage to take place.
The kind of malware you might encounter during the holiday season could be:
- Keyloggers: Keyloggers record your keystrokes which are sent to the bad actor. Typically they’re used to collect usernames and passwords. This allows the bad actor to then log into your account. Keyloggers can be embedded in a malicious website, it can be a standalone program, or it can run on a USB dongle.
- Web skimmers: A web skimmer is a piece of malicious code that’s embedded on a payment page of a web store that collects your payment information for your credit or debit card.
- Ransomware: Ransomware is on the destructive side of things. It locks up your files, or your computer, or access to your network. In order to get access to whatever is locked up, you need to pay a ransom. Typically the ransom is paid using cryptocurrency such as Bitcoin.
- Banking trojans: Trojan horse malware is a program that purports to do something legitimate, and does said function, while also carrying out malicious activities. A banking trojan typically targets mobile devices. They are used to steal bank login information, text messages containing one-time passwords, and credit card information.
How does someone get their device infected with malware?
A common way someone gets infected is through email that contains a malicious link or attachment. They may look like links to invoices, or a PDF, or a spreadsheet, or a document file labeled in a way to entice you to open them. If the email is text only, the chances of getting infected by opening it up are pretty non-existent. There may be some email service providers that allow multimedia attachments like images, audio, or video to run. This increases the chances of being infected. However some email service providers won’t load multimedia attachments without your permission.
Malware is also delivered over text message that typically contain a malicious link. There is a variant of this where no link is used, but through some clever social engineering, gets you to reply to a text message and that’s where the scam begins. You can read about this over at Krebs On Security.
There’s also been an increase in QR code phishing (AKA Quishing).
QR codes are everywhere.
They’re on fliers, business cards, mobile tickets, and restaurant menus. This is just a drop in the bucket for where they’re found. Over the last several months there’s been an uptick in QR code phishing and it’s been primarily observed over email. The bad actors are either embedding QR codes directly in the email, or they’re attaching PDFs with QR codes as a way to bypass email spam filters. To get you to scan the QR code, they may tell you that you have to scan the QR code for verification purposes. Once you scan it, one of a couple of things could happen. You’ll be greeted with a form to fill out asking for sensitive information, or the link you’re directed to could infect your device with malware. Since this particular article is themed around holiday shopping, our educated guess is you’ll probably see this applied to the “undelivered package” scam, which we have an example later on, or an invoice, or an unrealistic discount for an item you’d love to purchase as a gift. Since QR codes are out in the wild, someone may get creative and design a Holiday themed flier, so keep your wits about you if you’re out and about in the real world.
Malware is sometimes found on legitimate websites and the services they use to serve up ads. If these sites and services are compromised there is potential for your device to get infected. There are websites that are set up intentionally to infect visitors too and the bad actors may set them to be an evil twin of their legitimate counterpart.
Your mobile app stores contain malicious applications. Sometimes they look similar to legitimate well known applications in both design and name. Other times they blend in with popular types of apps making the selection process that more important.
How to know if you’re infected
First, depending on the malware, you may not know. If it’s a new virus, for example, it can still infect your computer or phone even if you have anti-virus on it. This is because the anti-virus vendors don’t know of its existence yet and hasn’t been added to the virus definitions. The bad actors are always looking for new ways to evade detection. With that being said, here are some indicators that your computer or mobile device is infected:
- Your device seems like it’s running slowly. If it’s due to an infection it’s because stuff is hogging computing resources, but not all malware sucks up all this bandwidth. If your device is old, it’s expected to slow down over time. In other words, a slow device can either be attributed to age or malware, so run a full virus scan to see if anything is discovered.
- You see a lot of ads or popup windows.
- You notice icons of applications on your device you’ve never installed.
- In the case of ransomware, locked files/folders and a ransom note are clear indicators of infection.
- Your devices are constantly crashing.
- Your anti-virus alerts you.
Some ways to help proactively reduce your chances of getting your devices infected
- Install antivirus on your devices and make sure the software and virus definitions are up to date. Make sure you schedule full antivirus scans to run nightly. To note, iPhones and iPads do not have antivirus currently available for them because of how they’re designed. Your Mac on the other hand needs antivirus.
- Make sure all of your devices and software are up to date. This helps patch up security holes discovered by the vendor.
- Lock your devices! Whether it’s a password, PIN, fingerprint, or facial recognition, have something in place to prevent someone getting physical access to your device. With online accounts, make sure you have two factor authentication enabled.
- With mobile devices, and we’re including laptops for this tip, do not leave them unattended, especially if you do venture out to a store or mall to do shopping. Where you go, so does the device.
- Don’t click, or tap, on links in emails, text messages, QR codes, or social media posts(or DMs) that look strange. Don’t open suspicious attachments, even if it’s coming from someone you know(Tip: If you know the person find a different way to contact them to verify what they sent you). If you’re asked to browse to a website, make sure the name is spelled correctly. Also make sure the email address of the sender is also legitimate. If you’re expecting something from Disney, they wouldn’t contact you from a Gmail account.
- Do your due diligence when installing apps. Make sure it’s from a trusted source. Read the reviews left by users. Read the app permissions to see what the app wants to request access to on your device. If it seems off, like a flashlight app that requests access to your device’s storage, that’s a red flag. Also make sure the name of the app isn’t misspelled or have additional text added to it. For example if you’re installing TikTok, the real one in your app store is just “TikTok.” If you see something like “TikTok Official App” that’s a red flag.
- Install trusted web browser plugins like adblockers or third party tracker blockers. These will help reduce the chances of malware laced ads from infecting your devices. The same due diligence is needed with installing web browser extensions as some are malicious, so the same warnings in the point above apply.
Now that we’ve covered social engineering and malware, lets explore a few examples of different scams/phishing attempts that’s related to the holiday shopping season.
Here’s an example of a fake PayPal invoice with an incorrect item that’s purchased. This is an order confirmation scam. The scammer is looking for you to give them personal and/or financial information if you contact them. Pro-tip: Don’t use the contact information in any suspicious communication you receive. You’ll end up interacting with the bad actor. Go directly to the source to contact someone. In this instance you would go directly to paypal.com. Whether or not you have a PayPal account use this link to report a scam https://www.paypal.com/us/webapps/mpp/security/report-problem
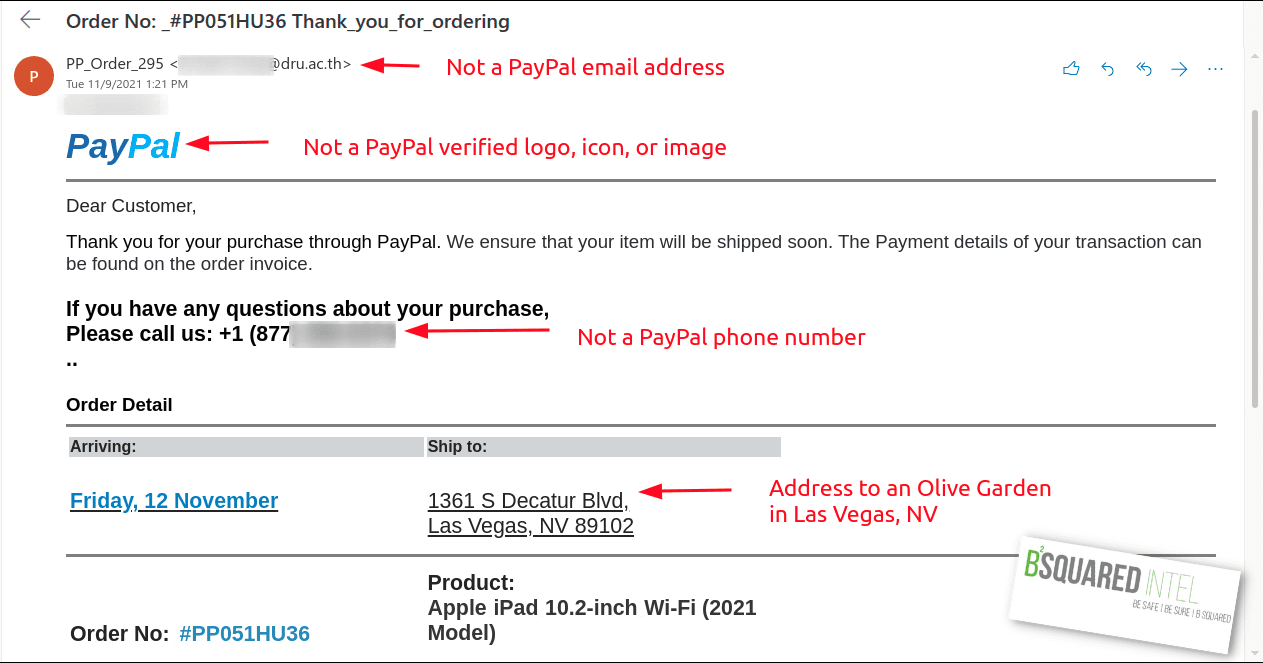
In the image above, you’ll notice that the email sender is not PayPal, the phone number doesn’t belong to them either, nor is the logo an official one from the company. When it comes to an emotional trigger, this may illicit a sense of panic that you either purchased the wrong thing, someone made an unauthorized purchase, or you put in the wrong shipping address.
The next image is an “undelivered package” scam.
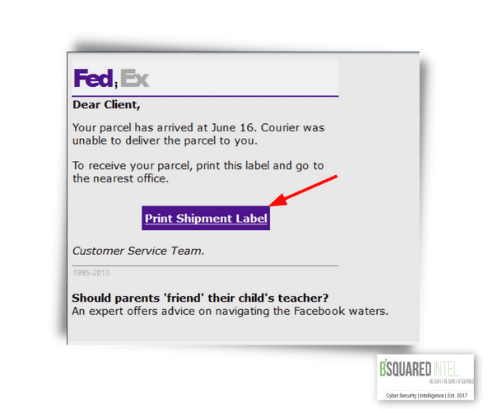
So, what’s wrong with this email?
First the FedEx logo is wrong and a semi-colon (;) is inserted between “Fed” and “Ex.” The real dangerous part of this email is clicking on the link for the shipping label. This is where your device may be infected or be asked to fill out a form that wants you to provide sensitive information.
The reason why this scam succeeds is if you’ve bought a lot of gifts from different places at different times, your inbox will have several package tracking notifications and this one may blend in.
This next image is the SMiShing version of an “undelivered package” scam this time pretending to come from USPS. The redacted phone number is not the USPS, the redacted name isn’t us, and the partially redacted link isn’t tied to the USPS because it ends with .info. If you would like to track your packages, use the post office’s tracking tool https://tools.usps.com/go/TrackConfirmAction!input.action
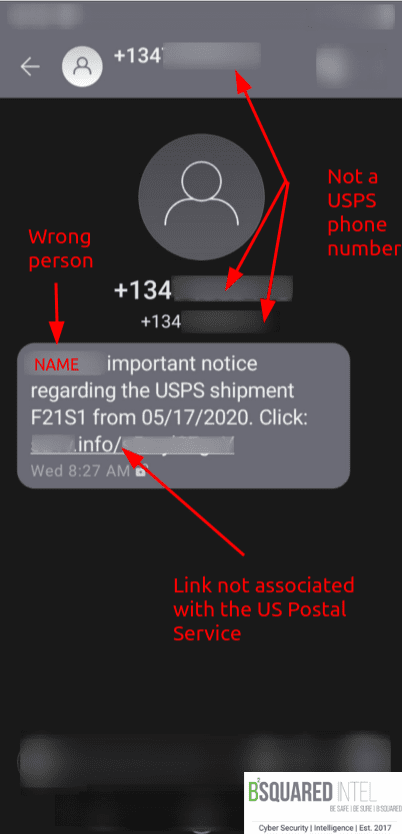
Now let’s get into some shopping scams.
With these scams, some of the telltale signs are the use of shortened links(e.g. https://bit.ly/3cGSaac. which links to our home page bsquaredintel.com), websites names that look similar to a real company, super low prices, and language to compel you to buy (e.g. “One day sale,” “limited supply). This is Social Engineering 101.
In the hands of a bad actor, link shortening services are used to disguise a real malicious link. You can use a tool like https://unshorten.me to view where a shortened link will take you before deciding to browse to it. Try it with the shortened link in the first sentence of the paragraph above.
Similar looking names are meant to deceive you because at a quick glance it may look real, even more so if you’re in a hurry. If someone wants to make you believe their malicious site is real, they may misspell the name where the “typo” looks close to the real domain name. They may use a domain name that may have the same top level domain(TLD) like .com but it might look something like blackfriday[YEAR]-[name of company].com (This is known a combosquatting where someone adds a word in front of the real domain name.). They may even use the wrong TLD, so if the legitimate company uses .com they may use .net.
The super low prices are to trigger the impulse buying. The “One day sale” or “limited supply” language imposes a time crunch to compel you to act now.
This image below was from a Facebook post found in the wild last year. What makes this post suspicious is the unrealistic discount and the fake domain names.
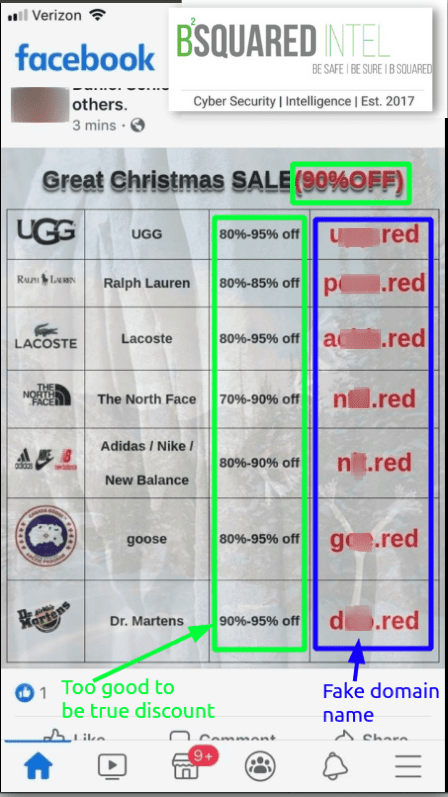
This next Facebook post is one of the greatest hits that pops up every now and again.

Indicators that this is a fake ad:
- The domain name is not the real one for Ray Ban.
- The discount is unrealistic.
- “one day sale” language to create scarcity and to trigger impulse buying.
This last piece of work is probably our favorite. It is a fake website that has all the trimmings; an online catalog, contact information, and so much more that we created a separate article on this one. These images that we’re showing are to illustrate that these prices are obscenely low for things like bounce houses and playground sets. This was discovered a couple of years ago, so the real product names might not be the same, but the pricing for items like these on Walmart, or Amazon, are hundreds of dollars to about two thousand dollars.
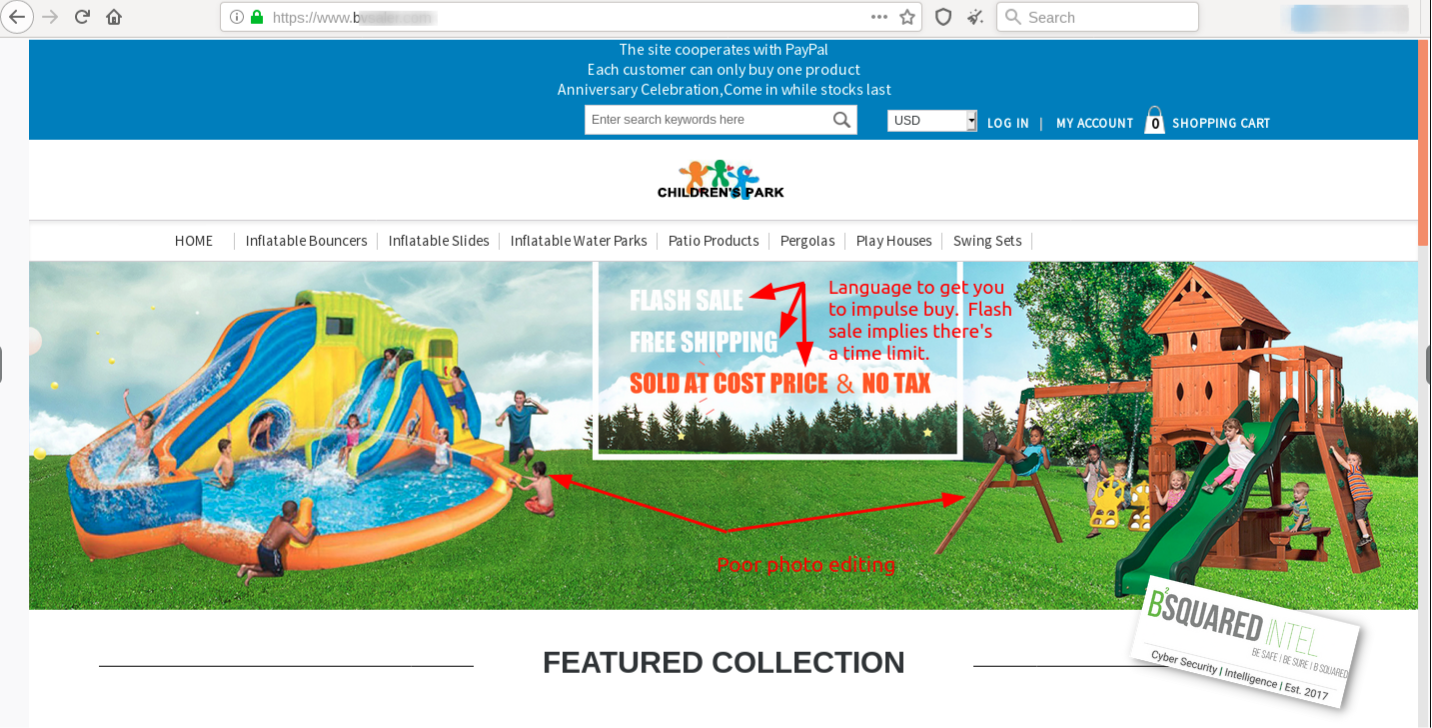
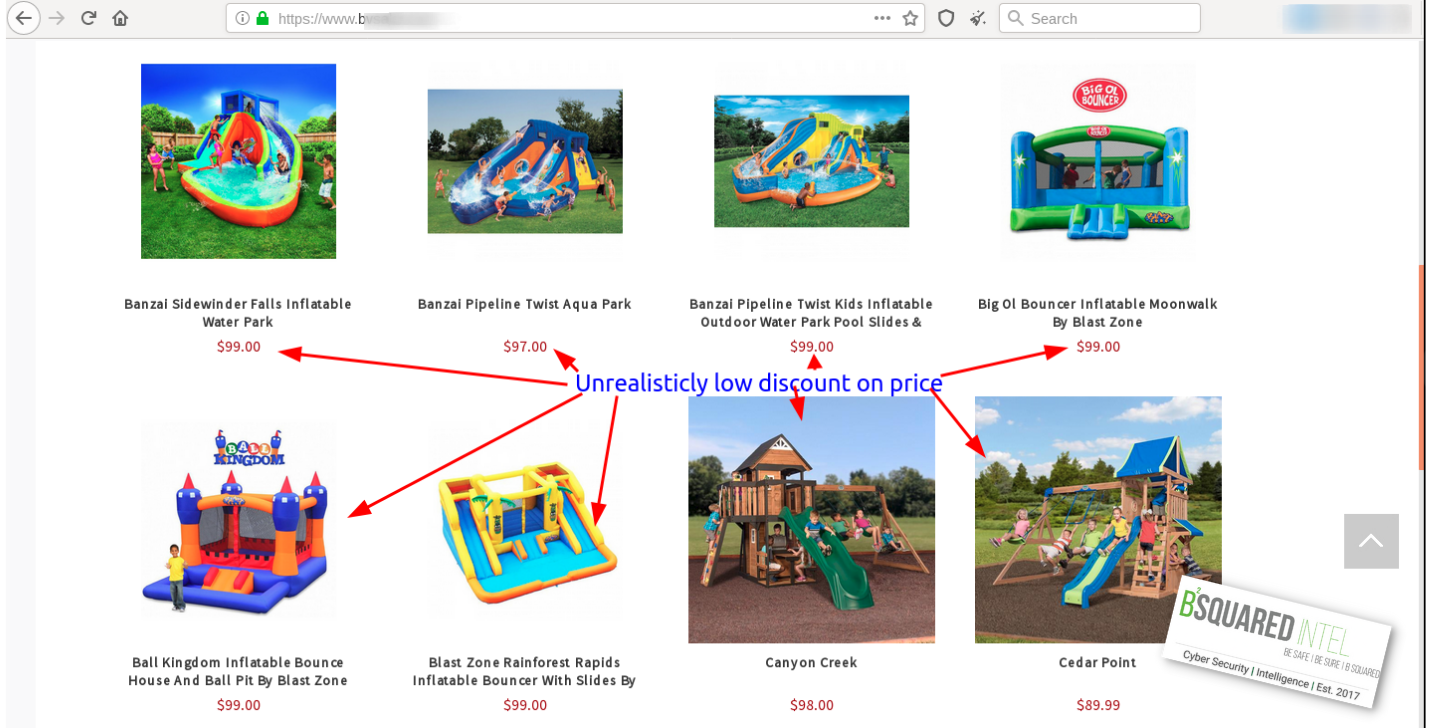
Lastly, we can’t forget about stuff that happens in the real world. If you’re going shopping at some point you might need to grab some cash at an ATM for stuff or fill up the gas tank at the gas station. We wrote an article on how to look out for skimming and shimming devices at the ATM or gas pump. You can read it here.
For a safer personal shopping experience this holiday season, and everyday for that matter, here are some tips for you:
- Be aware of confirmation and undelivered package scams.
- Scrutinize deals you see on social media and websites. If it looks to good to be true, it’s most likely a scam.
- Be aware of suspicious looking online payment pages.
- When making online purchases, make sure the site is secure. You’ll see a padlock typically to the left of the URL or you might see this symbol
 and the URL itself will begin with HTTPS. As a reminder, seeing that a website is using HTTPS doesn’t mean it’s a trusted site. It only means that your communications from your device to the site is secured, so due diligence is needed before you enter your payment information.
and the URL itself will begin with HTTPS. As a reminder, seeing that a website is using HTTPS doesn’t mean it’s a trusted site. It only means that your communications from your device to the site is secured, so due diligence is needed before you enter your payment information. - Pay with a credit card instead of a debit card. If something goes wrong, you aren’t putting your bank account at risk.
- Monitor your bank, credit card, and other financial statements. Also monitor your health insurance and medical bills for anything suspicious.
- Be aware of online surveys that you may take. Malicious ones will start asking for personally identifiable information(PII) like credit card information and other personal stuff. Do not provide this information willingly.
- Make sure you have anti-virus on your devices, that it’s up to date, the virus definitions are up to date too, and that you have a full scan scheduled to run nightly. Also make sure your devices and other applications are up to date too.
- Avoid public WiFi when out shopping. If you must connect, use a Virtual Private Network (VPN) to add a layer of protection. In case you need a VPN service, we are independent partners for Proton Technologies. Their product is ProtonVPN. Click our affiliate link here to purchase an account.
Why are we telling you all of this?
In 2022, cybercrime, according to the FBI’s Internet Crime Report, cost victims $10.3 Billion USD.
- Phishing/Vishing/Smishing/Pharming victims totaled 300,497 down 7.5% from 2021 where there were 323,972 reported criminal complaints, which is still a lot. Total losses in this category is $52,089,159.
- Identity theft victims totaled 27,922 down 59.6% from 2021 where there were 51,629 reported criminal complaints. Total losses in this category is $189,205,793.
- Confidence Fraud/Romance victims totaled 19,021 down about 24% from 2021 where there were 19,47324,299 reported criminal complaints. Total losses in this category is $735,882,192.
- Ransomware victims totaled 2,385 down about 44% from 2021 where there were 3,729 reported criminal complaints. Victims losses from ransomware were $34,353,237. These numbers could be way off too because not everyone is going to report this incident, and it doesn’t include loss of revenue, downtime, costs of third party help, etc.
Read the FBI’s 2022 Internet Crime Report here
For those concerned with elder fraud, especially during the holiday season, the FBI’s annual report for elder fraud has a listing of scams, statistics, and helpful tips for protecting your elder loved ones, friends, and neighbors. Read the report here.
Note that the FBI’s reporting doesn’t account for unreported incidents, so it’s hard to tell what the real number for victims and losses are.
What happens to your stolen data and how much is it worth?
Your stolen data gets sold on the “dark web” or via other channels. Through our research here are some findings:
- Batches of stolen credit card data range from a little over $100 to just shy of $1000. The higher price for certain batches is due to the fact that the the credit cards have a high limit like $25,000. While on the topic of stolen credit cards they can also be cloned by transferring the data to blank cards and then be sold. These cloned cards can then be used to make purchases.
- Combo lists, which contain stolen login credentials from multiple data breaches, can go for roughly $100 – $2000 depending on the size of the list.
- Stolen email addresses, that can be used for spam and phishing, range anywhere from twenty to a couple of hundred dollars. These email addresses are obtained either through data breaches or web scraping efforts.
- A stolen social security number with a date of birth runs as little as $1.
How we protect you and your family
Check out our Personal Services to better protect you and your family. We provide services ranging from *identity theft protection and restoration, to education, to digital footprint reviews. Click here for more information.
We also have our Web Digital Literacy course, which helps you build the fundamental skills you need to survive in the online world, or add more skills to what you already know. You’ll learn how to pick apart websites and the content you consume. Click here for more information.
*A note on the identity theft protection and restoration services. If you suspect that your identity was stolen and you are going to sign up for the service, contact us before doing anything else.
Finally, let’s shift over to businesses.
Business owners, it’s your turn now
Pretty much everything up to this point is applicable in some way, shape or form for your company. Here is a good summary of things to do to protect your organization during the holiday shopping season and beyond:
- Educate employees on how to spot social engineering/phishing attacks. One click of a bad link is all that’s needed to compromise your business and your customers. Cybersecurity awareness training is important.
- Search the web for fake websites and social media profiles posing as your organization. Document everything you can about them and then report them.
- Search the web for pictures you use for your company. This includes your logo(s), branding material, and products. Other intellectual property includes things like copy and proprietary items such as design plans, processes, or code.
- Ensure that if you are accepting payments yourself, and not using a platform like PayPal/Venmo, Square, Stripe, Zelle, Apple Pay, etc, that the payment portal is secure; the same goes for any form submission or login of your website. This means making sure that you have TLS certificates in place to encrypt client and server web traffic. Also if you are accepting and processing payments yourself you’ll need to be PCI compliant.
- Ensure that all all devices, software, and websites are patched and up to date to plug up any known security holes.
- Monitor your financial statements and cash flow.
- For employees that need access to computing resources to do their job, limit their access. Operate on the practice of Least Privilege by only assigning staff the least amount of access to resources that still allow them to carry out their daily duties unhindered.
- Lock sensitive physical documents up if you need access to them. Shred these documents if no longer needed.
- Given the timing of this post, your mileage may vary logistically.
- Invest in security cameras and an alarm system to protect your physical inventory.
- Purchase a cyber liability insurance policy to have some recourse if your company is compromised.
- Adhere to cybersecurity frameworks to better strengthen your organization. If you are a business in Connecticut, these articles we published are a primer for you on the State’s cybersecurity and data privacy laws
To learn more about our businesses services, click here.
We provide everything from consulting, assisting with cybersecurity frameworks, to external cyber risk/threat assessments, to other custom services such as looking for stolen intellectual property on the Internet-at-large.
Below are helpful things for everyone if you experience something that needs reporting.
Documenting things and resources for reporting incidents:
- Get screenshots of everything (emails, texts, websites, social media profiles/posts/DMs).
- Save email headers.
- Have your bank and credit card issuer’s contact information handy.
- The Federal Trade Commission (FTC)
- For reporting fraud: https://reportfraud.ftc.gov/#/?pid=B
- To report identity theft: https://www.identitytheft.gov/#/
- The Federal Bureau of Investigation
- To file a criminal complaint: https://www.ic3.gov/Home/FileComplaint.
- You can also call your local field office for assistance.
- The United States Postal Inspection Service
- To file a report https://www.uspis.gov/report
- If you see any scams, fake sales/contests/giveaways, or fake profiles on social media, use the platform’s reporting tools.
We hope you found this article helpful to survive the holiday shopping season and beyond. Share this with those you think will find it helpful.
If you come across any interesting holiday shopping scams whether in your emails, texts, social media, or on the web, we’d love to hear about your finds in our contact form below and if you want to learn about our services also use the same form.
Lastly if you’re interested in signing up for our newsletter to get cybersecurity and intelligence news, tips, tricks, and tools, the registration link is https://bsquaredintel.com/newsletter-signup/
Be safe out there. And however you define family, we hope you’re able to spend time with them.
Happy Thanksgiving and Happy Holidays!
Please fill out the form below, or call 203.828.0012, to learn how bsquared intel can assist you.Contact Us | Bsquared Intel


 and the URL itself will begin with HTTPS. As a reminder, seeing that a website is using HTTPS doesn’t mean it’s a trusted site. It only means that your communications from your device to the site is secured, so due diligence is needed before you enter your payment information.
and the URL itself will begin with HTTPS. As a reminder, seeing that a website is using HTTPS doesn’t mean it’s a trusted site. It only means that your communications from your device to the site is secured, so due diligence is needed before you enter your payment information.